"Security is a process, not a moment in time." — Glow engineering handbook
1. Why Did Glow Choose a Guarded Launch ?
Glow's core contracts went live on Ethereum mainnet on 18 December 2023 under an intentionally conservative guarded launch framework.
A guarded launch adds explicit safeguards to brand‑new protocols so that—if the unexpected strikes—users can be made whole without resorting to ad‑hoc governance fixes.
The Glow protocol's guarded launch consisted of the following properties:
- Address allow‑list. Only externally owned addresses (EOAs) and pre‑vetted contracts can hold core protocol tokens. This prevents malicious contracts from atomically exploiting freshly deployed logic. It also keeps tokens from slipping into external ecosystems. This sacrifices composability to eliminate integration‑breakage and migration risk, closing multiple layers of attack surface while the protocol hardens.
- Circuit breaker. A single on‑chain flag can freeze all transfers if anomalous behaviour is detected, buying engineers the time needed for a patch or controlled migration.
- Rollback plan. Should a critical bug slip through, contracts can be forked and state replayed from the block immediately before the incident.
- USDC Safety Net. The Glow protocol launched with USDG, a stablecoin backed 1:1 with USDC that would eventually be reedemable for USDC.
The guard did a good job of ensuring that people's money would stay safe, but it was partially incomplete.
2. USDG: Glow's One‑to‑One USDC Safety Valve
To ensure there is always a clear, dollar‑denominated asset that works within the guard, Glow issued USDG, a stablecoin pegged 1:1 for USDC held in a multisig controlled by the Glow foundation.
Transactions follow an atomic, two‑step flow:
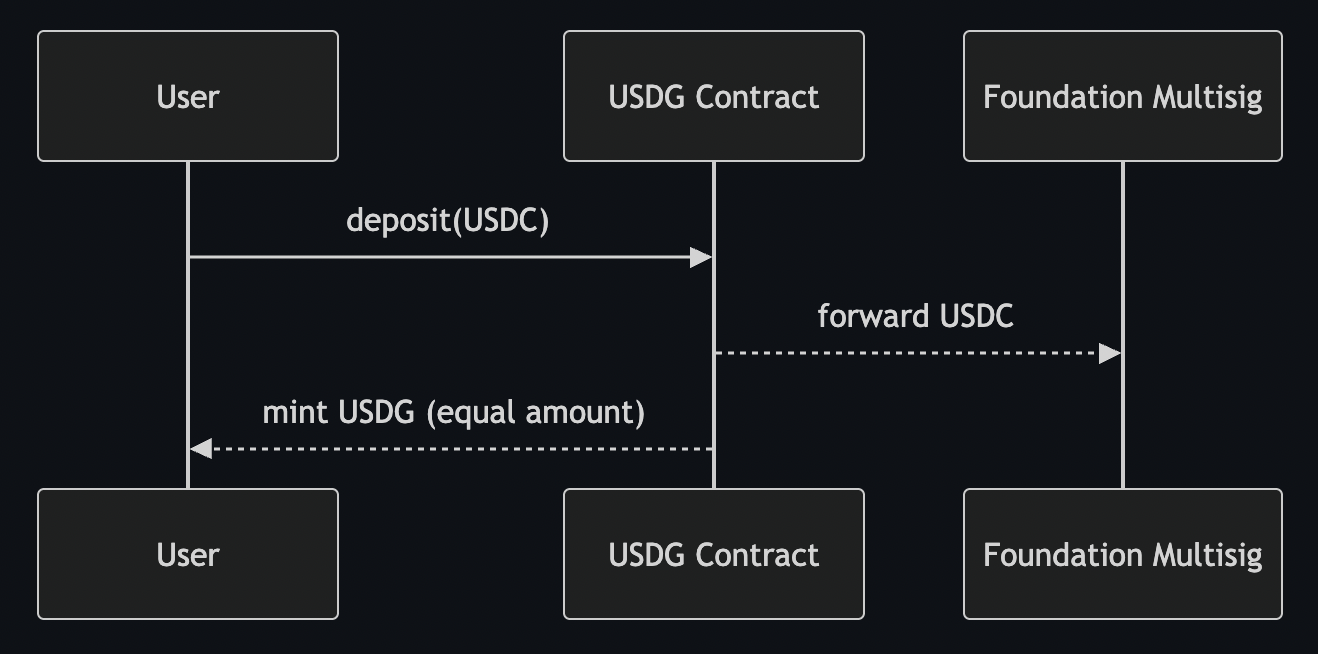
During minting the contract validates two critical constraints:
permanentlyFreezeTransfers == false– the circuit breaker must be off- Recipient is not a contract (unless that contract is on the allow‑list)
1function _update(address from, address to, uint256 value) internal override {
2 if (permanentlyFreezeTransfers) revert ErrPermanentlyFrozen();
3 _revertIfNotAllowlistedContract(from);
4 _revertIfNotAllowlistedContract(to);
5 super._update(from, to, value);
6}The original design did not include a path for redeeming USDG. This meant that the guard was like a half-built bridge. Users could enter, and know that their money was safe, but they could not get their money back.
3. What's New: Audited, Trustless Redemptions
While operating under its guarded launch, Glow cleared several major milestones. Over that period, virtually every core mechanic had been battle-tested in production, giving the engineering team confidence that enabling USDC redemptions carried no undue risk to the protocol.
At the time, users could mint USDG but had to wait for the redemption path to be fully vetted. Over the following months, the Glow team had designed and implemented the redemption system from the ground up, carefully integrating it into the broader protocol. After completing a thorough external audit with Spearbit, the contract is now green‑lit and slated for deployment.
3.1 How the Contract Works
- User calls
exchange(amount)supplyingamountof USDG
- The contract performs an atomic swap:
- Transfers
amountof USDG to0xFFfF...FFFf(the canonical burn address) - Pulls the same
amountof USDC from the foundation pool and sends it to the user
- Transfers
Because the burn address has no bytecode, the guarded‑launch checks see it as an EOA; the transfer therefore cannot be blocked by the Guard.
3.2 Audit Highlights
| Topic | Risk | Mitigation |
|---|---|---|
Re‑entrancy on exchange | ✗ | nonReentrant modifier |
| Insufficient USDC buffer | ✗ | Phased top‑ups governed by multisig |
| Price‑oracle dependency | ✗ | None—redemption is fixed‑rate 1:1 |
Spearbit found no issues in the smart contract that was provided to be audited.
4. Operational Roll‑Out & Safety Controls
Bringing redemptions to life wasn't just a matter of deploying code—it required a carefully staged operational plan. Even with a fully audited system, the team prioritized layered safeguards to monitor flows, respond to edge cases, and limit potential blast radius.
This section outlines the real-world controls Glow put in place to ensure a stable, low-risk launch of USDG redemptions.
- Gradual funding The redemption pool receives USDC in capped tranches, keeping the maximum possible outflow well below the multisig's balance while dashboards are monitored.
- Unified emergency stop The original circuit breaker now covers both USDG transfers and redemptions; a single flag freezes the round‑trip.
- Off‑chain mirrors Every redemption event is streamed to an external logging cluster, where anomaly alerts trigger a PagerDuty rotation.
5. What This Means for Glow Participants
With redemptions enabled, the protocol enters a new phase of maturity. What was once a one-way entry into the guarded system is now a fully functional, bi-directional path. For users, this upgrade brings tangible improvements in liquidity, security, and transparency.
- Full round‑trip liquidity
- Stronger assurance
- Foundation accountability
6. Lessons Learnt
No security architecture is perfect from day one. This section distills the most important takeaways—lessons that may shape how future protocols think about launch stages, audits, and composability.
- Bridge the gap between theory and practice
- Audit after real‑world soak time, not before
- Compose carefully, then quickly
Glow's engineering team continues to prioritise measurable security work over headline features. Expect a follow‑up post with live dashboard links and a detailed post‑mortem of the first week's redemption flow.
